How did the internet change during the pandemic?
The fundamental work of network management plays an increasingly important role as network infrastructure becomes more complex.

With the evolution of modern technology in computing, network, and communication, enterprises are gradually dedicated to constructing computing systems and network infrastructure in order to accelerate their digital transformation in the face of competition.
Since the COVID-19 pandemic outburst in 2020, several large-scale cities have locked down, leading to the suspension of work in the office and learning from schools. Thus, Work From Home and Distance Learning became the options for enterprises and schools during the pandemic.
The demand for the internet and network facilities has surged more than ever before with the pandemic. However, when networks have become more necessary in people’s lives, the network’s performance, security and vulnerability to hacker attacks are also more severe. As such, the latency of the internet, data leakage, and extortion scams become the prioritized subjects for IT Administrators. As such, the normal operation of network systems and network security is important in every industry.
Due to the operation within multiple locations, large enterprises and chain stores of retailers have a tendency to adopt a decentralized network architecture. In other words, the headquarter (HQ) and all branches have their own IDC room and network devices. In addition, the network infrastructure of such large enterprises or chain stores of retailers usually consists of different devices from multi-venders to make the environment large and complex.
As a result, IT administrators need to maintain not only the network infrastructure in the HQ but also those in the branches. This task is very crucial because the service and quality of the internet directly affect the productivity and operation of enterprises and stores. Any interruption can cause tremendous loss in production and revenue. Therefore, it is conceivable that network management is a serious subject of late and enterprises usually also spend a lot of money in order to ensure that systems work effectively and efficiently.
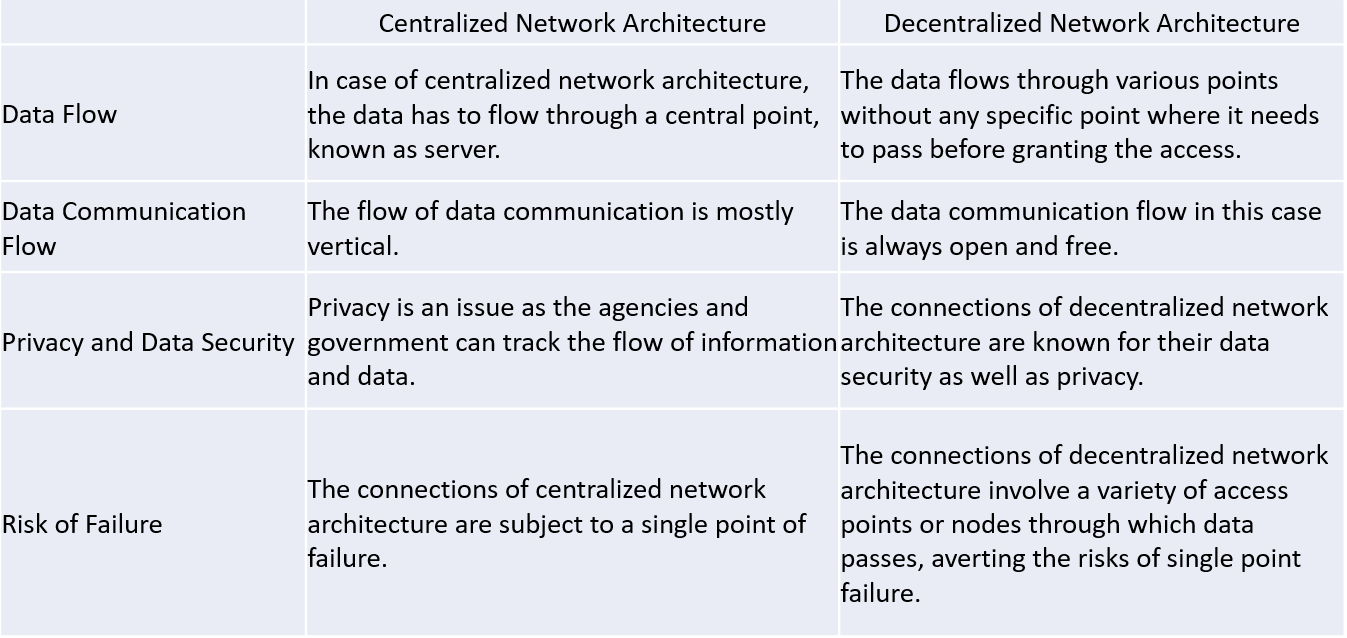
Chart 1- Comparison of centralized and decentralized network architecture
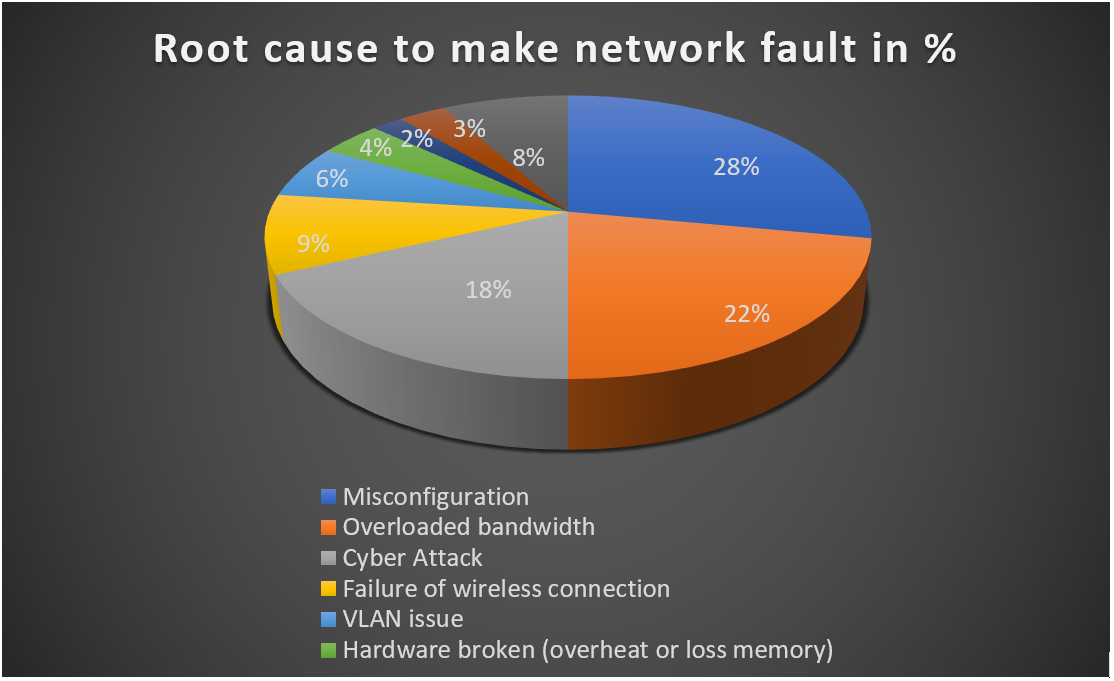
From the chart shown above, decentralized network architecture offers the benefit of allowing the data flow to be more flexible and open. Privacy and security are also much better than centralized architecture, however, it is also more critical for IT Administrators to find the root cause of the fault in the network system. According to the Garner report, 80% of the repair time for faulty internet is wasted in finding the root cause of the fault. The network performance and the productivity of an enterprise have a proportional relationship. In other words, high-efficiency network performance is beneficial for work productivity and brings positive development to the enterprise. From the below chart, around 50% of network faults are misconfiguration and overloaded bandwidth.
Strong network management software is therefore a necessary implementation in order to shorten the interruption of the service, caused by faults. It should be proactive to notify the fault rather than passively be called to help in the occurrence of problems.
Deciding on a good network management software is not an easy task. First of all, it has to be cross-platform and multi-vendor, simply because the complex infrastructure consists of diversified equipment. Secondly, the system has to build under the scope of 5M (FCAPS). FCAPS stands for Fault Management, Configuration Management, Accounting Management, Performance Management, and Security Management.
Fault Management
These are the fundamental features of the system to detect the fault in the system and then notify the IT Administrators. Real-time detection and notification are crucial since this is the main reason to install network management software. To achieve this, the system can always auto-discover the devices in the network system and build the inventory report for management purposes.
The further feature to auto-generate topology maps of the network system can also help IT Administrators realize its environment precisely and easily. It is advisable to diversify the method of notification to as many kinds of tools as possible. This could include popular apps on the smartphone to ensure IT Administrators receive them quickly. The dispatch of scripts toward the fault also means that actions can be taken immediately to rectify any issues. Since 80% of repair time is wasted in finding the location of the fault, the function of Fault Management helps prevent further interruption of network services.
Configuration Management
According to chart 2 above, 28% of fault is caused by misconfiguration over the network system. The feature of backup configuration could provide IT Administrators with the means to compare different versions for troubleshooting. The feature of restore configuration could ease the IT Administrators’ efforts to fix the misconfiguration by restoring previous versions.
Accounting Management
This feature gives monitoring and reports on the flow in particular channels, devices, groups, and areas. The data could provide IT Administrators a glance at the traffic and even for billing purposes. The issue of overloaded bandwidth can be proactively sorted by this management while the IT Administrator could analyze the volume of traffic sub to individual port levels to manage any abnormal abuse of internet resources instead of passively upgrading the bandwidth, which is costly.
Performance Management
Those features monitor the performance of the network environment from the bandwidth of each user, device, and group to the whole system. It analyzes the traffic and manages the NetFlow of users or groups to ensure the quality of service. The analysis could become the suggestion to extend the infrastructure.
Security Management
Network management could play a basic role in cyber security by monitoring the traffic from unfriendly sources like weblinks or servers. It could block those to prevent further attacks. It could also manage the behavior of users from internal system access to those sites.
Just recently, we found an interesting new player in the market for network management. It is known as Cyber Monitor. The developer claims it is an intelligent network analysis and monitoring system based on Web technology. It supports different browsers and has a unified interface that can cross-brand systems for monitoring. Cyber Monitor can manage network devices from different brands, whether IT, network security, OT, or other devices all can be managed. Its big data analysis is able to collect NetFlow, analyze abnormal network traffic, and quickly find the root cause of the fault.
They further claim it has passed the strict requirements of the telecom environment, complies with the Telecom Class 5M (FCAPS) management, and be able to meet the variable demands from different kinds of enterprises’ operation. It has been widely used in telecommunications, transportation, and enterprise industries to provide optimized network management services.
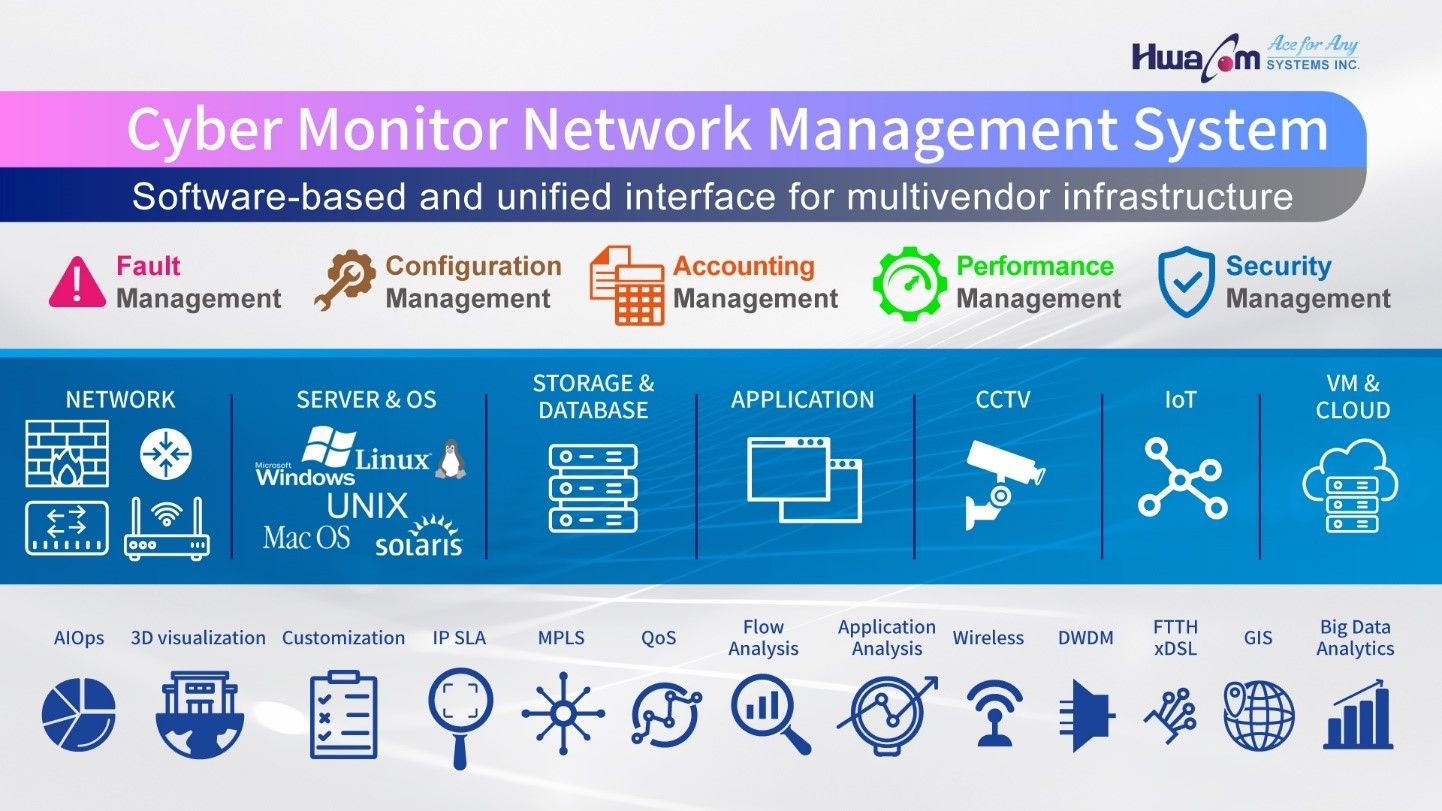
With more advanced topics, such as the capability to integrate with the AIOps module (which can predict and warn potential risks, define thresholds, and provide troubleshooting suggestions), the generation of variable log reports for IT Administrators and even 3D visualization IDC rooms are also in consideration for scalable demands.
There are many intelligent network management software in the market, such as Nagios, PRTG, SolarWinds and Cyber Monitor...etc. These brands of software are widely used in many enterprises, and each of them has its own advantages. For example, SolarWinds is one of the most active products in the market with a long history and provides a powerful system to offer rich features for different kinds of applications, but it needs IT Administrators trained in knowledge to operate its sophisticated system. In addition, SolarWinds requires the installation of many different modules and tools to perform its function.
The feature of PRTG is in line with expectations and is user-friendly. Cyber Monitor has been adapted in many different fields, such as telecom, transportation, manufacturing, and enterprises. It is also compatible with PRTG to offer much more features on the top. PRTG users could decide to upgrade to more powerful features of the Cyber Monitor package. Its unique position is to provide network management on decentralized network architecture as well as customization to build the exclusive and more friendly GUI, dashboard, and extra features to meet the demands of different industries. That is why it is popular in its home market.
Network management is not a new subject since the internet has been introduced for a long time now. However, this fundamental work plays an increasingly important role as network infrastructure becomes more complex and the service of the network becomes more crucial for the operation and productivity of the enterprises. Therefore, scalability and customization are good points to consider in the system since the entity and operation could be growing in the long scope.
About HwaCom System Inc.
HwaCom Systems Inc. was established in 1994(Stock Code 6163)and listed in OTC of Taiwan in 2002. HwaCom focuses on four key appliances, including ICT, Multimedia, Smart, and Security. Its base is from telecom, transportation, education, government, and enterprises. Its capability and experience support the company starting to develop its own products to meet the demand from the market, such as intelligent network management – Cyber Monitor. For more detail, please visit the product website:http://www.hwacom.com/web/cybermonitor/.
The mission of HwaCom is to build an international partnership and share its profound experience and capability via the essential products, it developed. In addition, HwaCom and its partners form an ecosystem to implement the new technology to enhance high effectiveness, efficiency, and modernization of the world.


